Harlan Carvey has given us a great tool in RegRipper and it’s undeniable that many examiners have found it to be a useful addition to their toolbox. RegRipper has a very specific purpose – parse the Windows registry. With some modification, we can turn RegRipper into WindowsRipper, an extremely powerful Windows triage tool. Using WindowsRipper we can parse much more than just the registry.
New Website
Matt's Twitter
- 4cast (1)
- aboutus (1)
- apple (3)
- attacks (1)
- authors (1)
- backontrack (1)
- backtrack (2)
- blog (1)
- botnet (1)
- breach (1)
- cell phone (2)
- cell phone forensics (2)
- cellebrite (1)
- chain of custody (1)
- challenge (1)
- copyright (1)
- crime (1)
- crypto (1)
- cyber security (6)
- cyber stalking (2)
- cybercrime (4)
- cyberwar (1)
- data size (1)
- economy (1)
- encase (1)
- encryption (3)
- enticement (1)
- evidence (3)
- exploit (3)
- facebook (4)
- fail (1)
- forensics (16)
- free (1)
- free speech (2)
- ftk (1)
- ftw (3)
- funny (1)
- future (1)
- game systems (2)
- government (1)
- gps (1)
- guidance (1)
- harassment (1)
- imaging (1)
- interview (6)
- investigation (8)
- ip (1)
- ip address (1)
- iphone (2)
- law (3)
- links (22)
- mac (2)
- model (1)
- news (16)
- pentest (2)
- podcast (1)
- printers (1)
- privacy (12)
- products (1)
- ps3 (1)
- quickhit (1)
- registry (1)
- regripper (2)
- review (1)
- riaa (1)
- sim card (1)
- skype (1)
- social engineering (2)
- social networking (1)
- theft (1)
- threats (8)
- tools (2)
- triage (1)
- Twitter (1)
- video (2)
- vpn (1)
Other Blogs
-
CYB3RCRIM3
-
LeftoversToGo.Com
-
A Geek Raised by Wolves
-
Forensic Focus
-
Microsoft® Malware Protection Center
-
Volatility
-
Windows Incident Response
-
Computer Forensics, Malware Analysis & Digital Investigations
-
Didier Stevens
-
Carnal0wnage Blog
-
Offensive Computing - Community Malicious code research and analysis
-
Forensics from the sausage factory
-
CyberSpeak's Podcast
-
geschonneck.com
-
int for(ensic){blog;}
-
Forensic Incident Response
-
ForensicZone
-
Computer Forensics/E-Discovery Tips/Tricks and Information
-
SANS Computer Forensics, Investigation, and Response
After the Facebook post last week, much of the backlash consisted of, "Who cares if someone has my IP address? That information is almost always out there." Well, here is a great example of what someone can do with an IP address.
Here’s something to really think about.. I was able to obtain all of the information in this post for 16 cents and by just using an email and IP address from a piece of spam.
Family members, ages, schools, anniversary dates, marriage lengths, hobbies, interests, phone numbers, addresses, property records, property taxes, pictures of their house, pictures of them, pictures of their children and grandchildren, deeds on their house, bankruptcies, employment history, previous addresses, previous creditors, and bits of social security numbers.
I’m pretty sure I’d be able to fake my way through one of those password reset forms.. you know, where you set up a “secret question” asking what your dogs name was, or where you went to school?
Beyond that, I’m fairly confident that at this point, if I were to call his bank and pretend to be him, I could easily pass when they asked me personal questions.
Hi all...
I just don't seem to write as many posts as I'd like, but I don't want this space to go to waste. If you have some topics you'd like to write about, please let me know. I'd love to add some new authors to this blog.
Let me know at matt @ binint.com or DM on Twitter @_remnant_.
Facebook is rolling out the new Privacy options today. There are a couple good things and a couple bad things. I suggest reading this article by the EFF for a good breakdown on the new changes. Sadly, your friends still have some bearing over how your information is used. In my opinion, Applications still get way too much leeway on what personal information they are able to see, collect, and use.
To maximize your privacy, I suggest the following changes. This guide should walk you through each screen and make sure you don't miss anything important.
The basic Privacy Settings screen looks like this:
 Start with the first group, Profile Information. There are several settings to update and every choice within this group should be set to "Friends Only". You'll have to click the Edit Settings button for Photo Albums and set each album to "Friends Only" as well.
Start with the first group, Profile Information. There are several settings to update and every choice within this group should be set to "Friends Only". You'll have to click the Edit Settings button for Photo Albums and set each album to "Friends Only" as well.

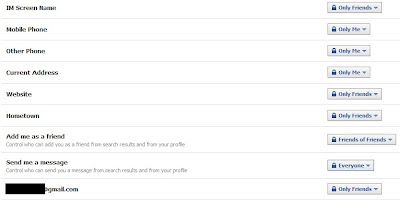
 The next group is Contact Information. This is how my settings look, but you may want to adjust for your own tastes.
The next group is Contact Information. This is how my settings look, but you may want to adjust for your own tastes.

The next group is Applications and Websites. The options here are:
 For "What you share", click on Learn More and you'll see an info screen. Click the link in the very last sentence or just go here.
For "What you share", click on Learn More and you'll see an info screen. Click the link in the very last sentence or just go here.
Click on "Edit Settings" for each application. Change the options to "Friends Only". You might want to look at the "Additional Permissions" to see if the application can post to your stream.
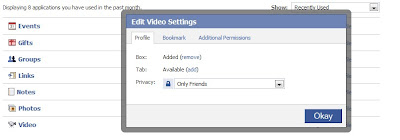 Also, on the top right of this screen there is the drop down box labeled "Show". Make sure you go through all of those screens so that you don't miss any applications.
Also, on the top right of this screen there is the drop down box labeled "Show". Make sure you go through all of those screens so that you don't miss any applications.
A quick note about Applications... make sure you delete any Applications you aren't using. Every application has access to your personal information and this really isn't a good thing. Take it straight from the creator of Mafia Wars.
The next group within Applications and Websites is "What Your Friends Can Share About You". Uncheck everything and then click Save Changes.
The last two sections, "Blocked Applications" and "Ignore Application Invites" probably don't need to be edited.
The fourth main section is Search. In this section you will need to Uncheck "Allow Indexing" and set "Appear in Search Results" to "Friends of Friends" or "Friends Only". This section will help restrict the general public from finding your profile. Again, the point of this article and the settings presented is to protect your privacy.
The last main section is Block List and probably doesn't need to be edited at this time.
Now we've walked through the main sections to protect your privacy. This is a great first step, but as the EFF article points out
Looking even closer at the new Facebook privacy changes, things get downright ugly when it comes to controlling who gets to see personal information such as your list of friends. Under the new regime, Facebook treats that information — along with your name, profile picture, current city, gender, networks, and the pages that you are a "fan" of — as "publicly available information" or "PAI."To help minimize what you're sharing with the public, you'll have to change some of this info as well.
To begin, click on "Edit My Profile" underneath your profile picture. Uncheck "Show my sex in my profile" and make sure the dropdown box underneath your birthday is set to "Don't show my birthday in my profile".
Next find the box on the lefthand pane that shows your friends. Click on the pencil and uncheck the box that says "Show my friends on my profile".
Your profile picture is displayed publicly despite your Photo Album settings. If you're not comfortable showing your picture to the world, change it to something else.
The final pieces of information will have to be removed entirely if you don't want them publicly displayed. Current City, Networks, Recent Activity, and Fan Pages are all publicly available. I deleted everything (although I really didn't have much to begin with).
To see how your new Profile looks to the public, click on Privacy Settings, Profile Information, and then Preview Profile. If there is any information displayed that you don't want, go back through the settings and remove it. Again, some things must be manually deleted.
After following these steps, the only information I have publicly displayed is my name, my fake profile picture, and one Fan Page.
Good luck changing your settings. If there was something I missed, please let me know in the comments. If you have trouble changing a setting, let me know that as well and I'll try to help you out.
Here is a news story that Jim and I participated in on Facebook and securing your private information.
http://www.wowt.com/home/headlines/67332677.html
Another article came along regarding Facebook security and hijacked applications. What I found most interesting was this quote:
On top of all these security issues, in August many Facebook users were surprised to discover the vast amounts of personal information they were revealing by their use of Facebook quizzes. Even if you limit access to your profile through privacy settings, Facebook quiz applications can see everything on your profile page when you take a quiz...or even when your friend takes one. To make matters worse, Facebook does not screen developers for trustworthiness nor do they require developers to comply with a privacy policy."...or even when your friend takes one." I've always thought that it's kind of shady that quizzes and applications can access my friends' personal data. I shy away from the apps and quizzes for this specific reason. But, are my friends providing me the same courtesy? By being on Facebook, am I putting my personal information security in my friends' hands? Facebook has done better with increased privacy settings, and hopefully users have changed those settings to be more restrictive.
If I was a malicious user, I would absolutely create as many quizzes as I could that would take advantage of the automatic data mining capabilities of Facebook.
It seems like a recurring theme on this blog lately, but be careful of what you post online.
Wow. We all know that social networking can be "bad". Here are a few recent articles.
- Exclusive: U.S. Spies Buy Stake in Firm That Monitors Blogs, Tweets
- How Social Networking Can Hurt You
- How Hackers Find Your Weak Spots
- Opinion: Twitter, Facebook Security Depends on Vigilant Developers, Sensible Users
- Researcher: Hackers Hijack Some Facebook Apps
- Facebook, Twitter users beware: Crooks are a mouse click away
- Does your social class determine your online social network?
Stan B. Walters is well known as "The Lie Guy". He gets a fair amount of press and I've attended his Kinesic Interview and Interrogation course. Stan often uses current events to illustrate his techniques and talking points. In his most recent blog post, he takes on the "Balloon Boy" family.
We now know that the balloon stunt was a hoax. Stan mentions that "it all came down to the verbal and nonverbal cues of deception generated by the Heenes." Unfortunately, he doesn't go into any detail on what he thinks those cues were. However, there are a few listed in the CNN article linked above.
Stan talks about narrative based interviews as a way of gathering information. You can learn a lot from just listening to someone talk and watching their body language. He also mentions that the interviewer needs to be aware of what signals they are giving back to the interviewee. These are a lot of the same points I tried to make in the Social Engineering Podcast and Stan's post is a good read.
I've been waiting for an Android phone to hit Verizon for a while, so I've been following some mobile phone blogs. This post from Boy Genius Report was interesting to me on the cell phone forensics front.
One of Cellebrite's selling points for forensic use is that they often get previews of new devices in order to get their units up to speed for use in the carrier's stores. The photos in the BGR post (if real) certainly give some credibility to that statement. I wonder if other cell forensic suites get similar updates.
I mentioned a few posts back that I've been helping contribute content over at Social-Engineer.org. Today they released their first podcast and I was lucky enough to be the interview guest. The podcast builds on this post I did a while back about interviewing techniques.
I think the podcast presents some useful information. Even though the topic is interrogation, pieces of the conversation should be useful in everyday interaction.
Give it a listen and let me know what you think. If you RSS and don't want to come back here to leave comments, hit me up on Twitter @_remnant_ .
Thanks to everyone over at Social-Engineer.org for making a great site and some fun times.
For those forensic folk that may have not have seen this, I did a review of FTK3 for the good folks over at Forensic 4Cast. Check it out here, http://4cast.whitfields.org/?p=438.
Also, follow the 4Cast guys on Twitter at @Schizophreud and @englishgit.
It's not hard to look around and see that people are posting way too much personal information online. There are tons of articles about it and now we can even find out if you're gay or straight.
Most of the information seems harmless and a lot of people don't care if others know about their personal lives. But how much trouble can it get you in to? One couple thinks their Twitter posts led to their burglary.
Is it that easy?! Let's find out...
Chirpcity.com let's you search tweets by location. I chose a random city from the list and then searched for all tweets mentioning "vacation".

How lucky that the first result includes a potential victim. I don't want to get a real person in trouble here and create a ready-made victim, so I'm blocking out all identifying information. Plus, I don't think this person is actually going to be gone for five weeks during the school year as their Twitter feed also says they're a student. See how quickly we can learn about someone?
Ok, so let's go look at Twitter profile.

Now we're getting somewhere. Our second webpage gave us their last name and website address. If we wanted to learn more we could check out their webpage to hopefully see what kind of stuff they might have we could steal. Now we just need to find out where they live. Cue Zabasearch.com!
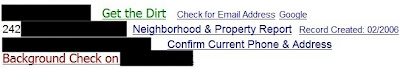
This was the most recent entry was for this person. I blacked out all the personal info so it doesn't look like much, but I now have a middle initial and possible address. I guess I could double check with other people searching sites. For a low monthly fee I could even subscribe to a data mining site and have instant information that includes much more than this!
Using free resources and five minutes of my time I located a potential victim and her address. I suppose it would be worth it to spend another 30 minutes and drive by the address to scope it out. Of course, if I really was a criminal I would have found multiple victims to go check out.
I guess it really is that easy. Be careful everybody!